
Berkenalan dengan Si Hijau Cecuer, Yuk!
AFPCSecure 4.0 - Check Portal. AFPC Secure. DoD Notice and Consent Banner. Click here to View the User Agreement. You are accessing a U.S. Government (USG) Information System (IS) that is provided for USG-authorized use only. By using this IS (which includes any device attached to this IS), you consent to the following conditions: -The USG.

Cara Membuat Jipang Khas Banten
SECURE meaning: 1. positioned or fixed firmly and correctly and therefore not likely to move, fall, or break: 2…. Learn more.

2FMA Chemical Route
SECURE is a workflow based system. In SECURE, the work name & work codes are received from Mahatma Gandhi NREGA MIS to the concerned Block/GP AE/Overseer login after the approval of Labour budget. The AE/Overseer of the Block/GP creates the detailed estimate, includes drawings, location map and photograph of the works site before starting the.
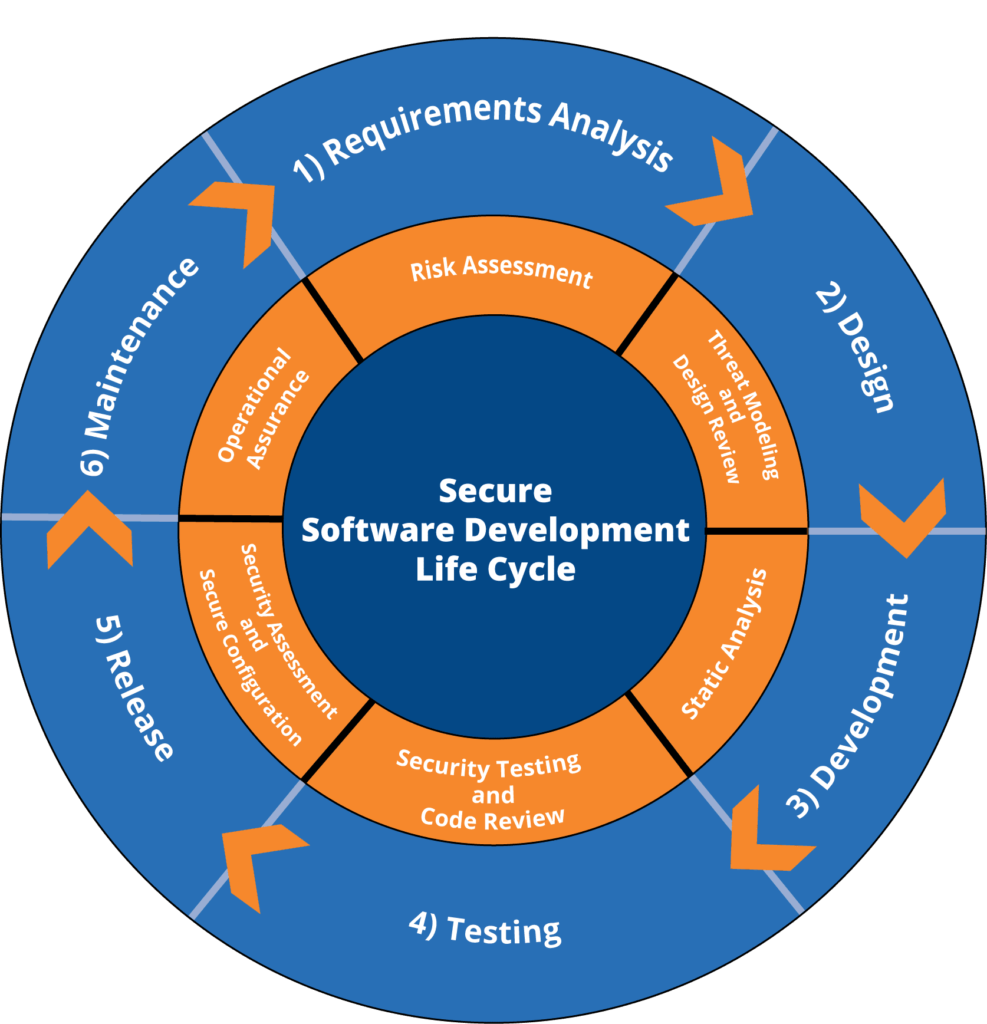
Secure Software Development Life Cycle Sdlc Introduction Sexiz Pix
Britannica Dictionary definition of SECURE. [or more secure; most secure] 1. a : protected from danger or harm. We need to make our network more secure against attacks by hackers. The children were safe and secure in their beds. A safe is provided to keep your valuables secure from potential thieves. b : providing protection from danger or harm.

Why You Need a Secure Network
SECURE - Synonyms, related words and examples | Cambridge English Thesaurus
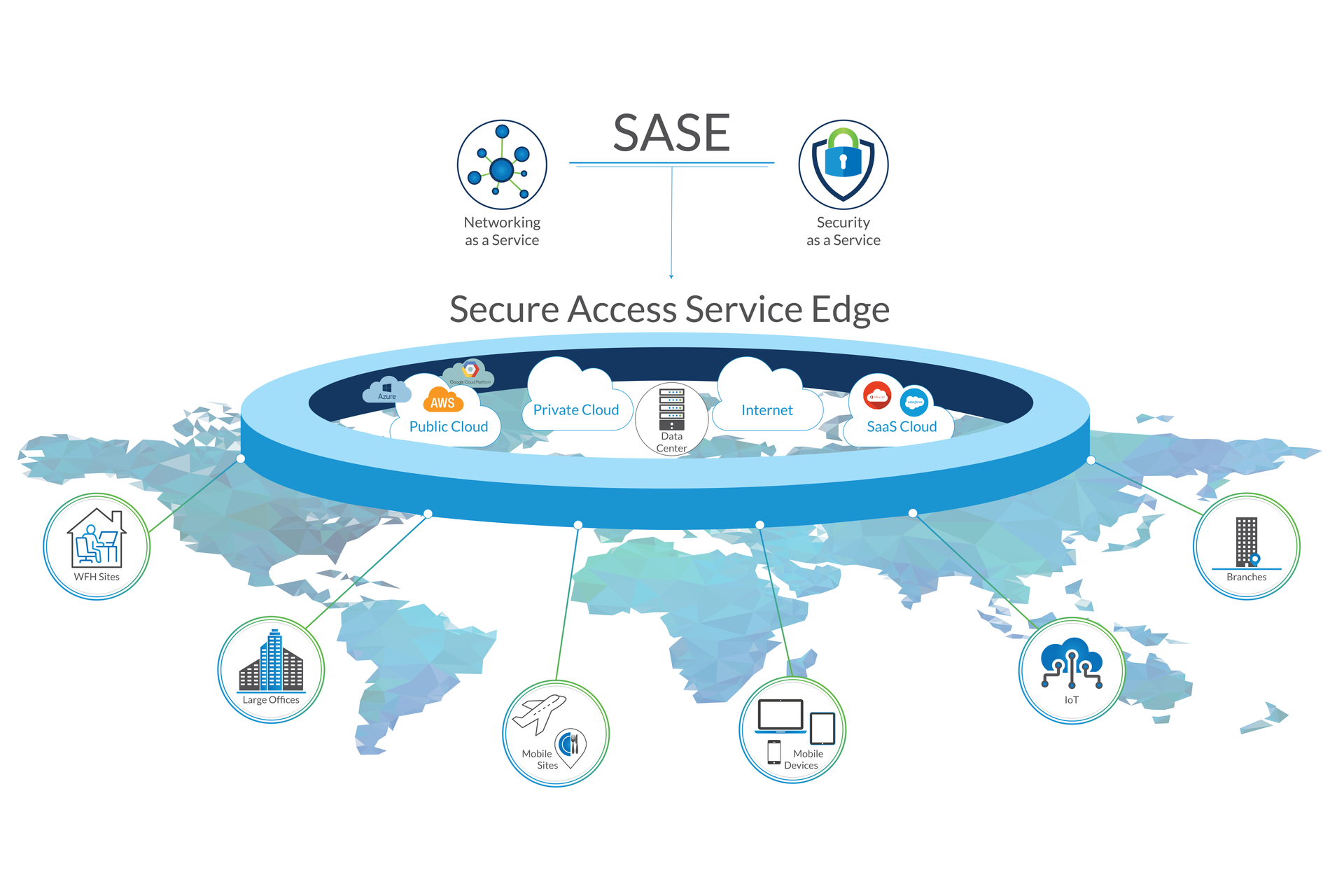
SiliconANGLE
Define secure. secure synonyms, secure pronunciation, secure translation, English dictionary definition of secure. adj. se·cur·er , se·cur·est 1. Free from danger or attack: a secure fortress. 2.

Secure stamp stock illustration. Illustration of grunge 18972709
Cecuer disajikan bersama parutan kelapa atau ampas kelapa dan ditabur dengan garam secukupnya. Jojorong; Kue jojorong merupakan kudapan khas Banteng yang bebahan dasar tepung beras, santan, dan gula merah. Mengutip dari disbudpar.pandeglangkab.go.id, dalam pembuatannya, kue ini juga menggunakan daun pandan untuk menambah aroma wangi kue jojorong.

10 Oleholeh Khas Tangerang Ada jajanan Unik Hingga Sirup
Based on this experience, we expect that high assurance memory safety can only be achieved via a Secure-by-Design approach centered around comprehensive adoption of languages with rigorous memory safety guarantees. As a consequence, we are considering a gradual transition towards memory-safe languages like Java, Go, and Rust.

How to Secure Cloud Storage 10 Tips to Keep Your Data Safe
Setelah cecuer matang, kemudian didinginkan dan dilepaskan dari cetakan. Cecuer dijual dalam bentuk berlapis-lapis. Menurut Alfiah, biasanya terdapat 10 lapisan dalam satu cecuer. Untuk membuatnya, setiap lapisan hanya perlu ditumpuk-tumpuk begitu saja. Setelah ditumpuk hingga jadi 10 lapis, setelah itu kue cecuer dibagi menjadi empat bagian.
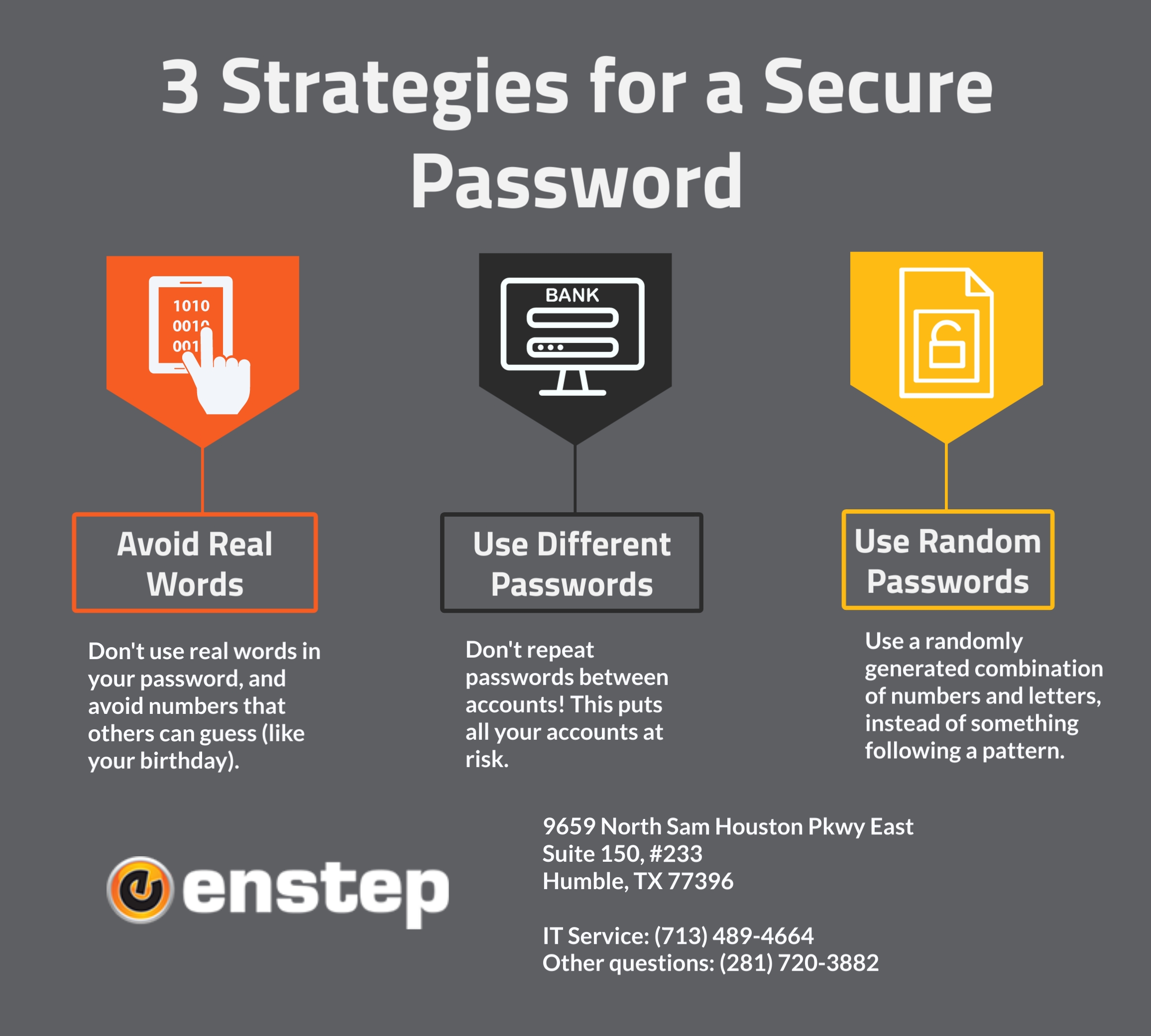
How To Keep Passwords Safe Soupcrazy1
secure: [adjective] unwisely free from fear or distrust : overconfident. easy in mind : confident. assured in opinion or expectation : having no doubt.
Pulse Secure YouTube
Collective Medical Client Portal: Log in to access your account and manage your care collaboration network. View patient profiles, alerts, care guidelines, and reports. Connect with other providers and share best practices.

Secure Infant Attachment Gooeybrains
A vulnerability in the SAML authentication process of Cisco Secure Client could allow an unauthenticated, remote attacker to conduct a carriage return line feed (CRLF) injection attack against a user. This vulnerability is due to insufficient validation of user-supplied input. An attacker could exploit this vulnerability by persuading a user to click a crafted link while establishing a VPN.

How to Develop a Secure Attachment Style
Revolutionize your enterprise security with Citrix Secure Private Access. Provide adaptive, Zero Trust Network Access (ZTNA) to IT-sanctioned apps for any user, anywhere, without the risks of VPNs. Enhance security for web, SaaS, and on-premises applications, ensuring safe, productive hybrid work environments. Discover how our solutions protect against unauthorized access, malware, and other.
secure payment icon for your website, mobile, presentation, and logo design. 20274016 Vector Art
With a win, the Buckeyes can secure sole possession of the Big Ten regular season title before heading to Iowa on March 3 for the season finale. It would mark OSU's first solo regular season title.

Distribution of solutions in the last iteration of CECuER dataset Download Scientific Diagram
Synonyms for SECURE: protect, defend, safeguard, guard, shield, keep, fence, fend; Antonyms of SECURE: attack, assault, assail, submit, overrun, yield, beset, cave

8 Password Best Practices to Secure Your Logins & Keep Your Personal Data Safe
Dell Secure Connect Gateway (SCG) Policy Manager, all versions, contain(s) a Stored Cross-Site Scripting Vulnerability in the Filters page. An adjacent network high privileged attacker could potentially exploit this vulnerability, leading to the storage of malicious HTML or JavaScript codes in a trusted application data store.