
Peluang Usaha Server Pulsa Jasa Server Pulsa
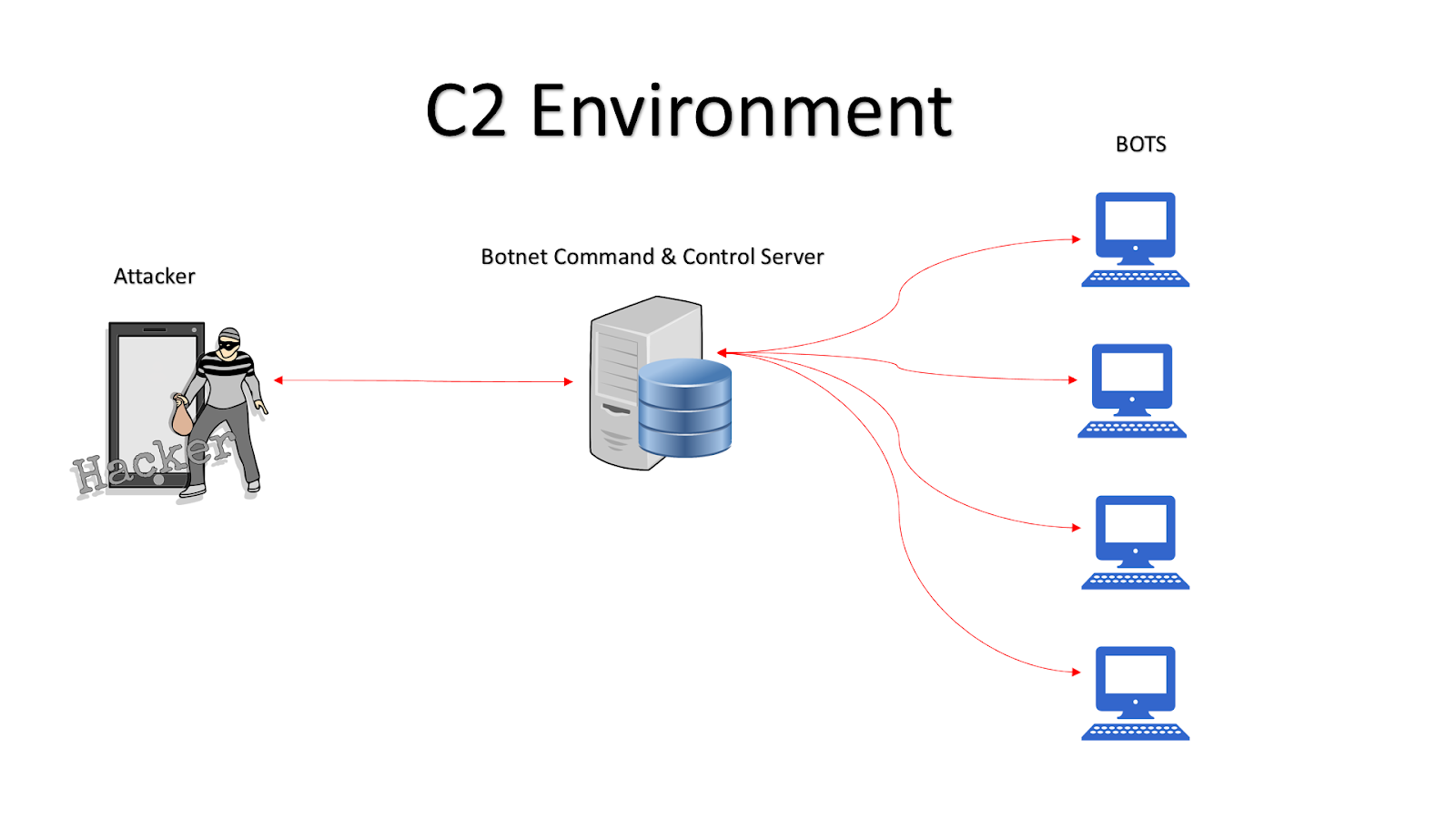
How C2 servers work. C2 servers operate by receiving and sending instructions and data to and from infected devices. Once a device is infected with the malware (also know as C2 agent, beacon), it establishes a connection to the C2 server, allowing the attacker to remotely control the device. The C2 server sends instructions over a C2 channel.

Cara Install Software C2 Metro Software Pulsa All Operator, Jasa Server Pulsa, Biller Pulsa
Command and Control Infrastructure, also known as C2 or C&C, is the set of tools and techniques that attackers use to maintain communication with compromised devices following initial exploitation. The specific mechanisms vary greatly between attacks, but C2 generally consists of one or more covert communication channels between devices in a.
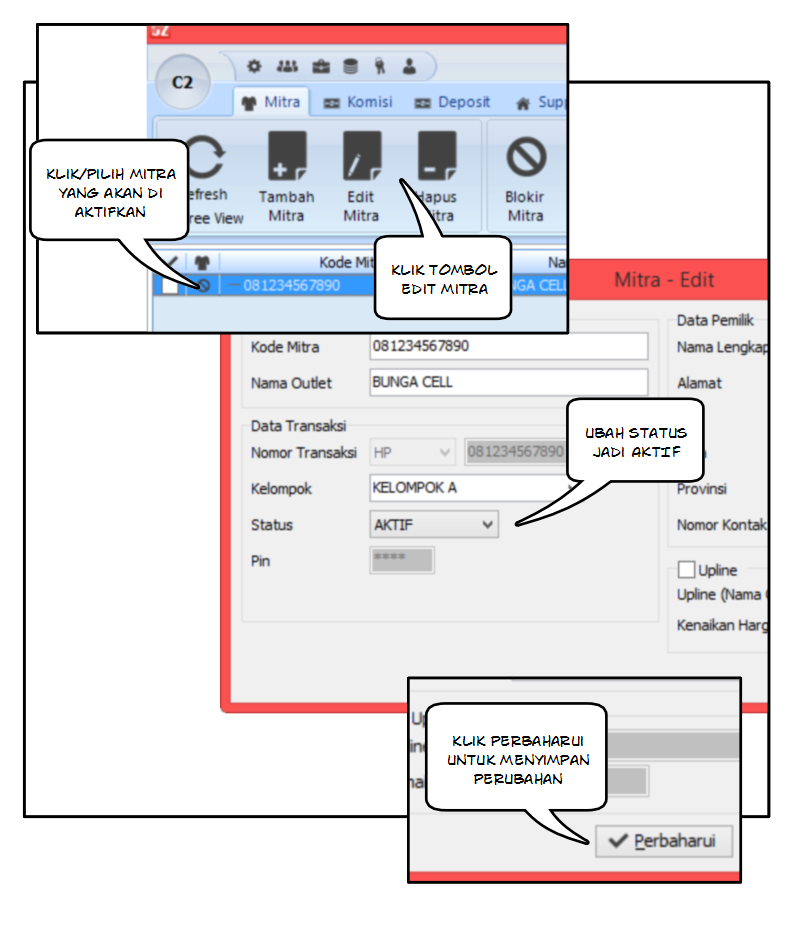
Cara Mengaktifkan Mitra di Software Pulsa Murah C2 Software Pulsa All Operator, Jasa Server
Stop malware by shutting down command-and-control communication channels. Command-and-control servers, also called C&C or C2, are used by attackers to maintain communications with compromised systems within a target network. The terms "command" and "control" are often bandied about without a clear understanding, even among some security.

Obfuscating Command and Control (C2) servers securely with Redirectors [Tutorial] Packt Hub
Jasa Server Pulsa by CV. Wijaya Komunika. Melayani jasa pembuatan server pulsa, paket data & PPOB dengan software Roket Pulsa, Penjualan paket server pulsa lengkap siap pakai + Training bagi pemula. Sudah 800 Lebih Server Pulsa di seluruh Indonesia menggunakan jasa kami. Free APK Android Trx via SMS, Telegram, Jabber/XMPP & Whatsapp
Jual SOFTWARE SERVER PULSA C2 METRO PROFESIONAL Shopee Indonesia
Command and Control servers, AKA C2 servers, are servers operated by threat actors and are used for maintaining communications with compromised systems within a target network. With the recent rise in double extortion ransomware campaigns, attackers are also sending exfiltrated data to C2 servers. Needless to say, one of our most important.
How to use Slack as C2 Sever
A command-and-control (C2) server is a main tool cyber threat actors have in their arsenal to launch and control cyber attacks. Threat actors use C2s to send commands to their malware and to distribute malicious programs, malicious scripts, and more. They also use them to receive stolen data that they exfiltrated from target servers, devices.

Red Team Tutorial Design and setup of C2 traffic redirectors by Dmitrijs Trizna Medium
Command-and-control (C2) servers are an essential part of ransomware, commodity, and nation-state attacks. They are used to control infected devices and perform malicious activities like downloading and launching payloads, controlling botnets, or commanding post-exploitation penetration frameworks to breach an organization as part of a ransomware attack.

Jual Paket Server Pulsa Otomax Lengkap Original di lapak ASP Corporation ID anugrahserverpulsa
One of the most damaging attacks, often executed over DNS, is accomplished through command and control, also called C2 or C&C. Command and control is defined as a technique used by threat actors to communicate with compromised devices over a network. C2 usually involves one or more covert channels, but depending on the attack, specific.
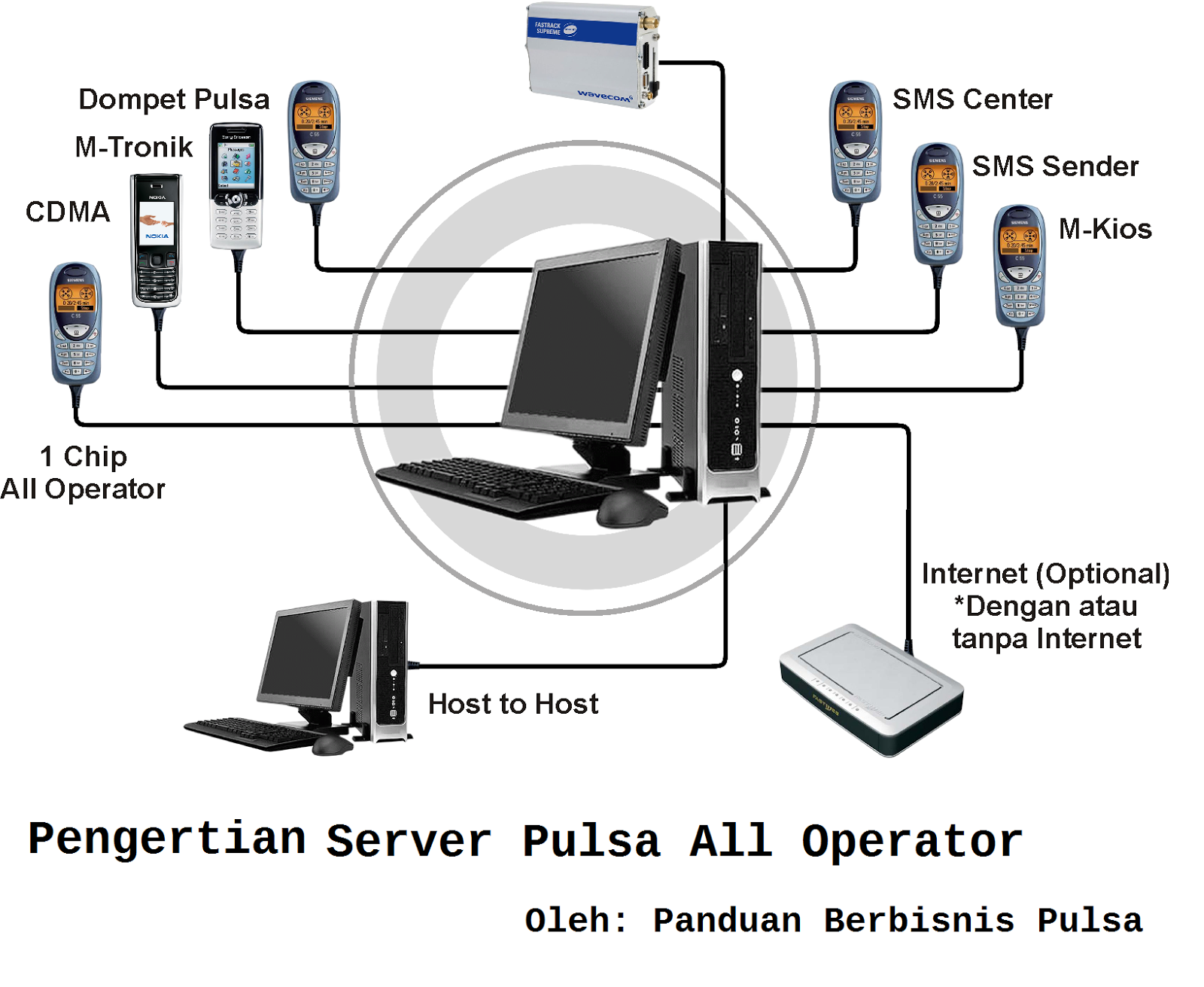
Pengertian Server Pulsa All Operator Panduan Bisnis Pulsa
A C2 server is one that a malicious actor uses like a general on the battlefield to command and control other machines-often whole networks of them-to carry out cyberattacks on their chosen targets. In the past, bad actors frequently ran their own physical C2 servers, but nowadays they are more likely to use cloud-based machines. Functions.

Cara Menjalankan C2 METRO Software Pulsa All Operator, Jasa Server Pulsa, Biller Pulsa Elektrik
The C2 agent periodically connects to the C2 server to check for commands. When the C2 agent receives a command, it executes the command on the compromised system. The C2 agent then returns the results of the command to the C2 server. The C2 server can be a standalone server or a cloud-based server. The C2 server is typically protected by.

Pembuatan Server Pulsa Dari Awal Sampai Siap Pakai ASP Corporation ID ServerPulsa YouTube
Keunggulan Bisnis Server Pulsa Kami. C-Software dirancang sebagai tools untuk menciptakan usaha yang mudah, murah dan pasti menguntungkan. Hanya dengan biaya layanan mulai Rp. 100.000 sebulan, dan biaya instalasi awal Rp. 1.000.000 Anda sudah dapat mengembangkan usaha server pulsa dengan layanan all in service yang kami sediakan.

11 Aplikasi Server Pulsa Terbaik dan Tercepat 2021 Caraqu
Introduction. Command and Control (C2) refers to the infrastructure and protocols used by threat actors to manage and coordinate malicious activities, such as data breaches, malware dissemination, and cyberattacks. Often, C2 acts as the nerve center for cybercriminals and state-sponsored hackers as they are often used to maintain control over.

Obfuscating Command and Control (C2) servers securely with Redirectors [Tutorial] Packt Hub
Paket Server 1 harga 3,5 juta anda dapat Software C2 Metro Standard, 5 modem wavecom, stok pulsa h2h 500rb. Garansi training sampai bisa.. PAKET SERVER PULSA 1 Kami menawarkan jasa pembuatan dan perakitan Server untuk Pulsa Elektrik, dengan berbagai pilihan dan paket menarik.

Cara Kerja Server Pulsa Pada Transaksi Jual Beli Pulsa
Figure 4 - Create the Shadow Workers C2 Server. Once Digital Ocean finishes creating the server, we will configure our DNS to point to the C2 server. Figure 5 - Creating DNS Entry for C2 Server. You then should have DNS entries for both your target web application (from Part 1) and the C2 server. Figure 6 - DNS Entries.

CARA MENAMBAH SUPPLIER DI C2 METRO STANDARD & PROFESSIONAL Software Pulsa All Operator, Jasa
Overview. Command-and-control servers (C2) servers are used by attacker to maintain communications with compromised systems within a target network. Using your preferred programming language, develop a C2 server to establish basic communications with an "attacker" controlled machine (can be a basic Linux server).

4 Langkah Sederhana Membangun Server Pulsa Sendiri TRENT TRONIK
Introduction: In the realm of cybersecurity, threat actors employ various techniques to compromise and control targeted systems. One key component of their arsenal is the Command and Control (C2) server. This article aims to delve into the world of C2 servers, exploring their purpose, functionality, and the role they play in cyberattacks.